ABSTRACT:
Information sharing is the key goal of Cloud Storage servers. It allows storage of sensitive and large volume of data with limited cost and high access benefits. Security must be in given due importance for the cloud data with utmost care to the data and confidence to the data owner. But this limits the utilization of data through plain text search. Hence an excellent methodology is required to match the keywords with encrypted cloud data. The proposed approach similarity measure of “coordinate matching” combined with “inner product similarity” quantitatively evaluates and matches all relevant data with search keyword to arrive at best results. This approach, each document is associated with a binary vector to represent a keyword contained in the document. The search keyword is also described as a binary vector, so the similarity could be exactly measured by the inner product of the query vector with the data vector. The inner product computation and the two multi-keyword ranked search over encrypted data (MRSE) schemes ensures data privacy and provides detailed information about the dynamic operation on the data set and index and hence improves the search experience of the user.
EXISTING SYSTEM:
• The large number of data users and documents in cloud is crucial for the search service to allow multi-keyword query and provide result similarity ranking to meet the effective data retrieval need.
• The searchable encryption focuses on single keyword search or Boolean keyword search, and rarely differentiates the search results.
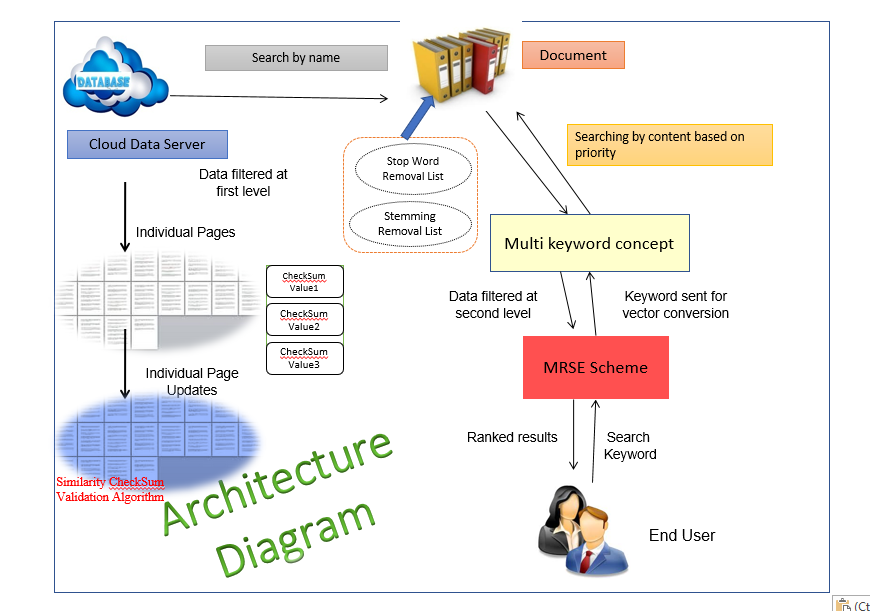
• By stop word concept the unwanted keywords will be removed.
• The document search by name not by content. so we get relevant information and irrelevant information.
• We are using MD5 algorithm in existing system.
Drawbacks of the Existing System:
- Single-keyword search without ranking
- Boolean- keyword search without ranking
- Multi-keyword ranked search over encrypted cloud data (MRSE)
- “Coordinate matching” by inner product similarity.
PROPOSED SYSTEM:
-
• We define and solve the challenging problem of privacy-preserving multi-keyword ranked search over encrypted cloud data (MRSE), and establish a set of strict privacy requirements for such a secure cloud data utilization system to become a reality.
• Among various multi-keyword semantics, we choose the efficient principle of “coordinate matching”.
• In proposed system define public or private page and will be stored .
• Individual page updation is in this system.
• We ranking the document(abc.doc) by multi key word concept.
• Checksum value for each page.
Merits of the Proposed System:
ARCHITECTURE:
SCREENSHOT:
SAMPLE CODE:
using System;
using System.Collections.Generic;
using System.Linq;
using System.Web;
using System.Web.UI;
using System.Web.UI.WebControls;
using System.Data;
using System.Text;
using System.Security.Cryptography;
using System.Xml;
using System.IO;
public partial class Register : System.Web.UI.Page
{
ConnectDB objConnect = new ConnectDB();
protected void Page_Load(object sender, EventArgs e)
{
}
protected void btnRegister_Click(object sender, EventArgs e)
{
lblMessage.Text = "";
try
{
if (txtFName.Text.Trim() != "" &&
txtUName.Text.Trim() != "" &&
txtPwd.Text.Trim() != "" &&
txtCPwd.Text.Trim() != "" &&
txtAns.Text.Trim() != "" &&
txtMobile.Text.Trim() != "" &&
txtDOB.Text.Trim() != "" &&
txtCity.Text.Trim() != "" &&
txtEmail.Text.Trim() != "")
{
if (txtPwd.Text.Trim() == txtCPwd.Text.Trim())
{
DataTable dtUser = objConnect.CreateUser(txtFName.Text.Trim(), txtLName.Text.Trim(),
txtUName.Text.Trim(), txtPwd.Text.Trim(), txtMobile.Text.Trim(),
txtDOB.Text.Trim(), ddlSecQns.SelectedItem.Text, txtAns.Text.Trim(), txtCity.Text.Trim(),
txtEmail.Text.Trim());
if (dtUser.Rows[0][0] != null)
{
lblMessage.Text = "User credentials registered successfully.";
}
else
{
lblMessage.Text = "Unable to register now. Please try later.";
}
}
else
{
ClearControls();
lblMessage.Text = "Passwords doesn't match";
}
}
else
{
ClearControls();
lblMessage.Text = "All fields are mandatory.";
}
}
catch (Exception ex)
{
lblMessage.Text = "Please try logging with your credentials, else register again.";
ClearControls();
Console.WriteLine(ex);
}
}
private string BuildXML(XmlDocument doc)
{
StringBuilder sb = new StringBuilder();
using (StringWriter sw = new StringWriter(sb))
{
XmlTextWriter tw = new XmlTextWriter(sw);
tw.Formatting = Formatting.Indented;
doc.WriteTo(tw);
}
return sb.ToString();
}
protected void btnCancel_Click(object sender, EventArgs e)
{
ClearControls();
}
private void ClearControls()
{
txtFName.Text = "";
txtLName.Text = "";
txtUName.Text = "";
txtPwd.Text = "";
txtCPwd.Text = "";
ddlSecQns.SelectedIndex = 0;
txtAns.Text = "";
txtMobile.Text = "";
txtDOB.Text = "";
txtCity.Text = "";
}
protected void btnBack_Click(object sender, EventArgs e)
{
Response.Redirect("Login.aspx");
}
}
using System;
using System.Collections.Generic;
using System.Linq;
using System.Web;
using System.Web.UI;
using System.Web.UI.WebControls;
using System.Data;
public partial class EnterApprovalPassword : System.Web.UI.Page
{
ConnectDB objConnect = new ConnectDB();
protected void Page_Load(object sender, EventArgs e)
{
if (!Page.IsPostBack)
{
if (Session["TowardsSecureUserName"] != null)
{
lblWelcome.Text = "Welcome " + Session["TowardsSecureUserName"].ToString();
}
else
Response.Redirect("Login.aspx");
BindApprovers();
BindDocs();
}
}
private void BindApprovers()
{
DataTable dtApp = objConnect.FetchApprovers(Convert.ToInt32(
Session["TowardsSecureUserId"].ToString()));
ddlApps.DataSource = dtApp;
ddlApps.DataTextField = "ApproverName";
ddlApps.DataValueField = "ApprovalUserId";
ddlApps.DataBind();
}
protected void lnkLogout_Click(object sender, EventArgs e)
{
Session["TowardsSecureUserName"] = null;
Session["TowardsSecureUserId"] = null;
Response.Redirect("Login.aspx");
}
protected void btnSubmit_Click(object sender, EventArgs e)
{
if (txtPwd.Text.Trim() != "")
{
int i = objConnect.SubmitPassword(Convert.ToInt32(Session["TowardsSecureUserId"].ToString()),
Convert.ToInt32(ddlApps.SelectedItem.Value), Convert.ToInt32(ddlDoc.SelectedItem.Value), txtPwd.Text);
lblError.Text = "Password submitted successfully.";
BindApprovers();
BindDocs();
}
}
protected void ddlApps_SelectedIndexChanged(object sender, EventArgs e)
{
BindDocs();
}
private void BindDocs()
{
if (ddlApps.Items.Count > 0)
{
DataTable dtDoc = objConnect.FetchDocsForApprover(Convert.ToInt32(ddlApps.SelectedItem.Value));
ddlDoc.DataSource = dtDoc;
ddlDoc.DataTextField = "FileName";
ddlDoc.DataValueField = "FileId";
ddlDoc.DataBind();
}
}
}
IMPLEMENTATION:
Module description :
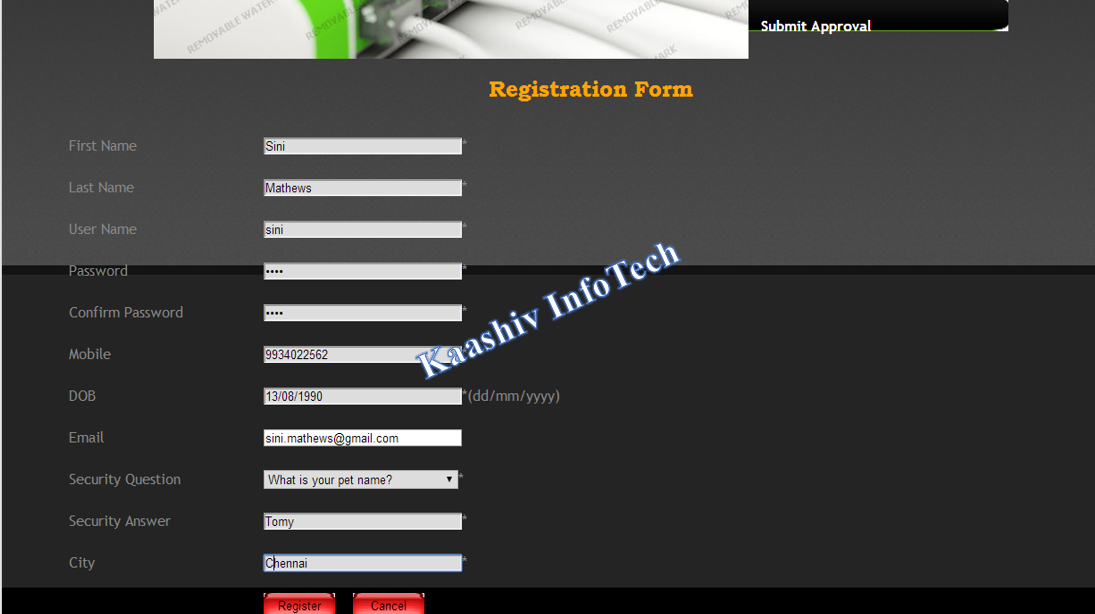
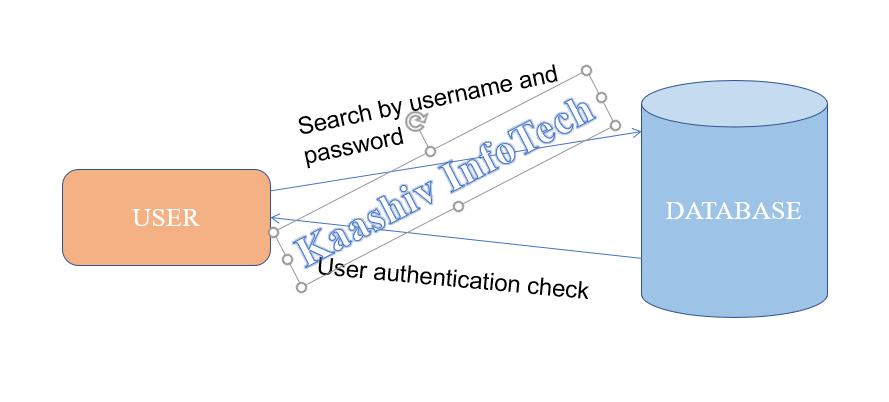
1.USER AUTHENTICATION MODULE:
• Authorized person can search for the document in the repository. In turn, unauthorized person cannot login into the system.
• To get an access, users are requested to create a valid user credentials.
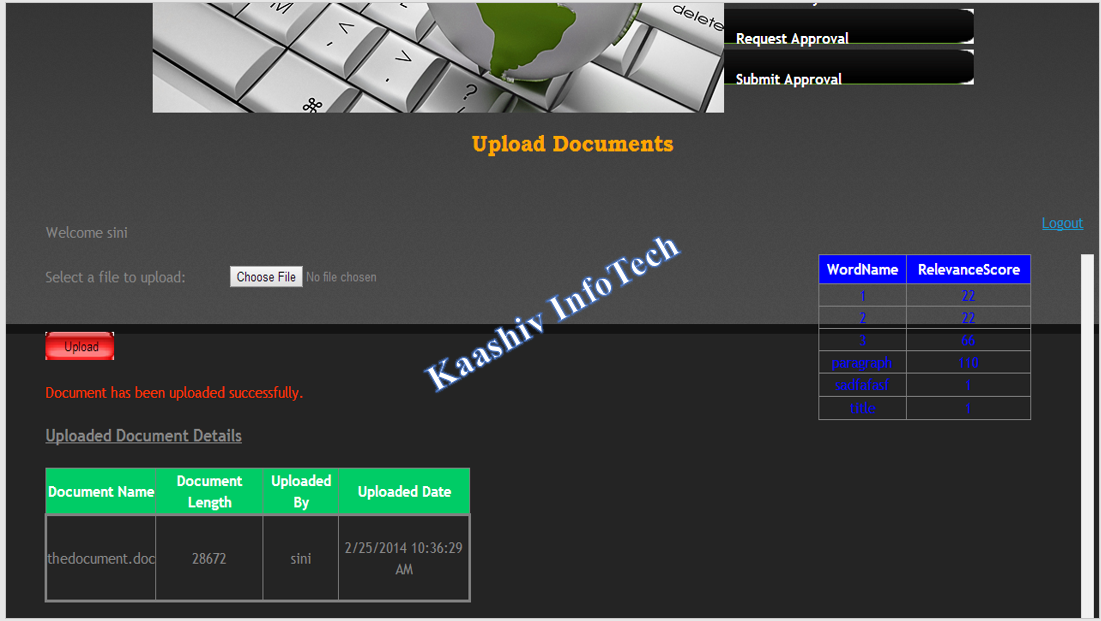
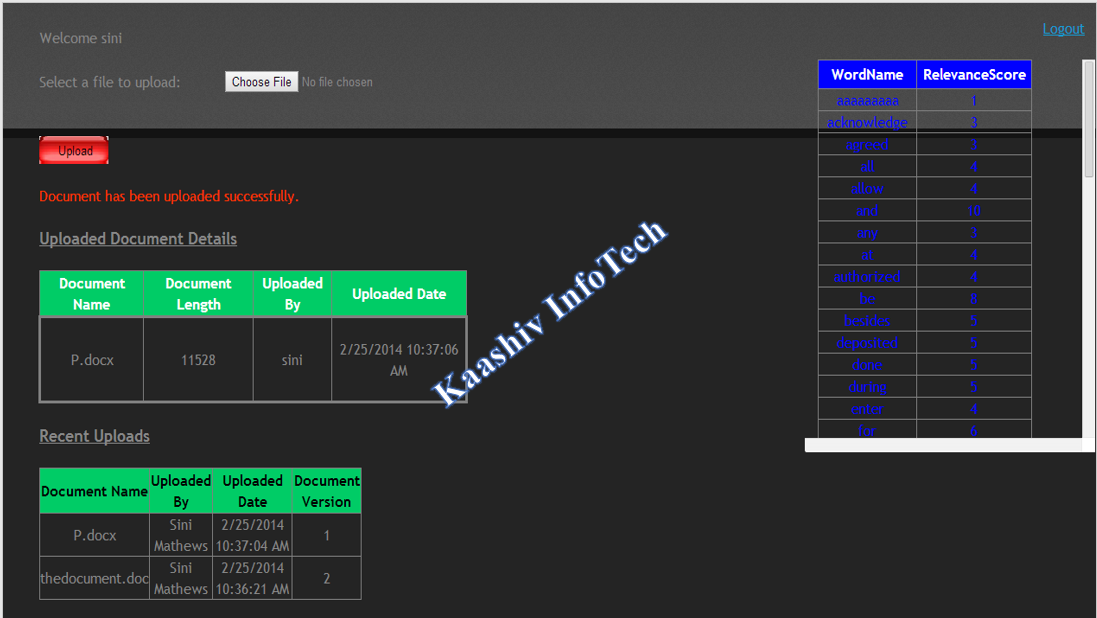
2.DOCUMENT UPLOAD MODULE:
-
• In this module, the user can load the documents into the system.
• Once the document is loaded, the entire keywords inside the document is parsed and loaded in to the database tables.
• The keywords were ranked based on the number of occurrences in the document. In turn, this can be optimized with unwanted keyword removal mining technique(stemming).

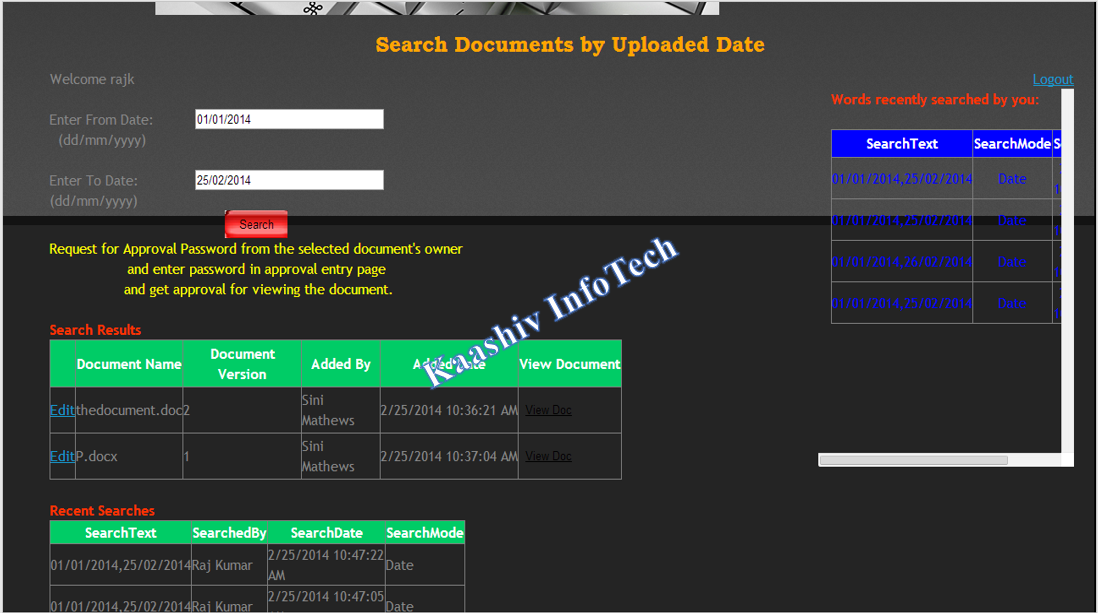
3. DOCUMENT SEARCH MODULE – Search by Doc Name, Search by Doc Date:
• After the verification of user’s information in a Database. User is allowed to search a document
• Using document name only. Each and every word is sorted and produce output based on name search in a database.
• Content-wise search is allowed in this Proposed System.
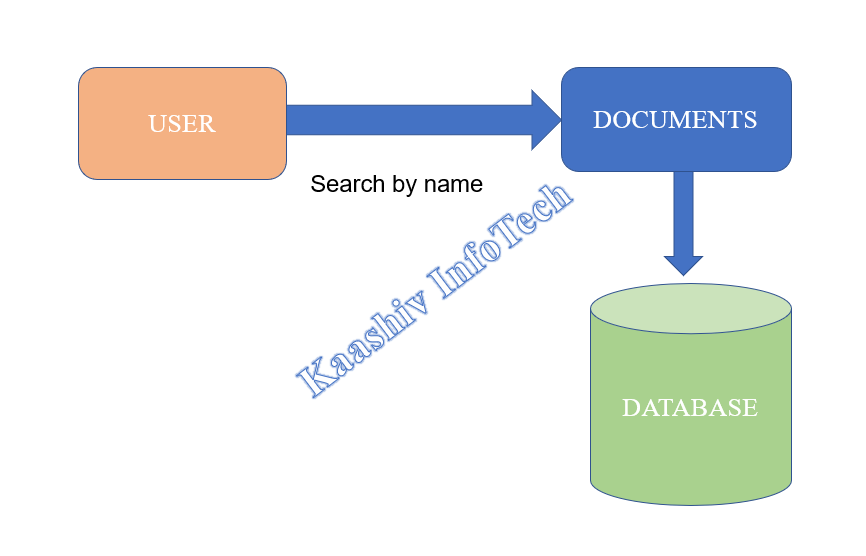
• Documents searched in a database by the order of document’s name and its content.
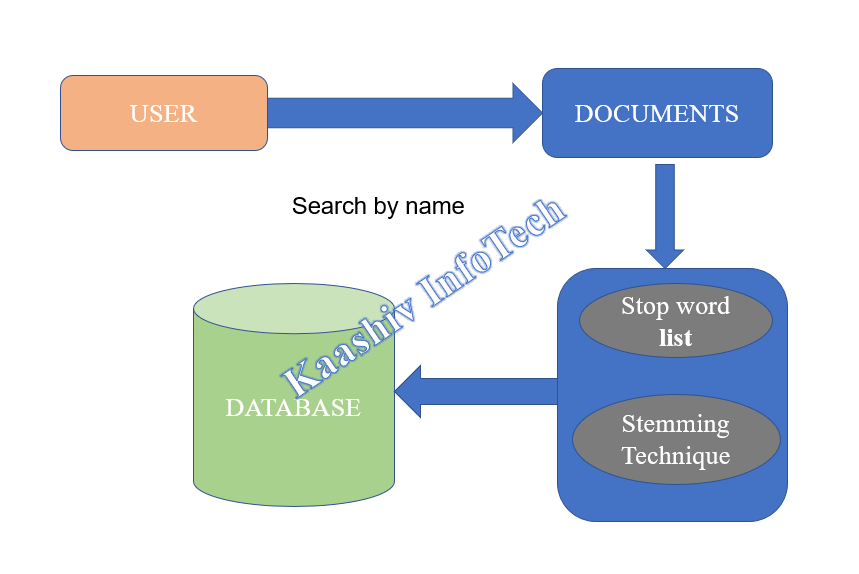
• Document‘s content is sorted by using stop word removal technique in a database.
• Stemming technique used to list the words by the removal of stemming words in a document
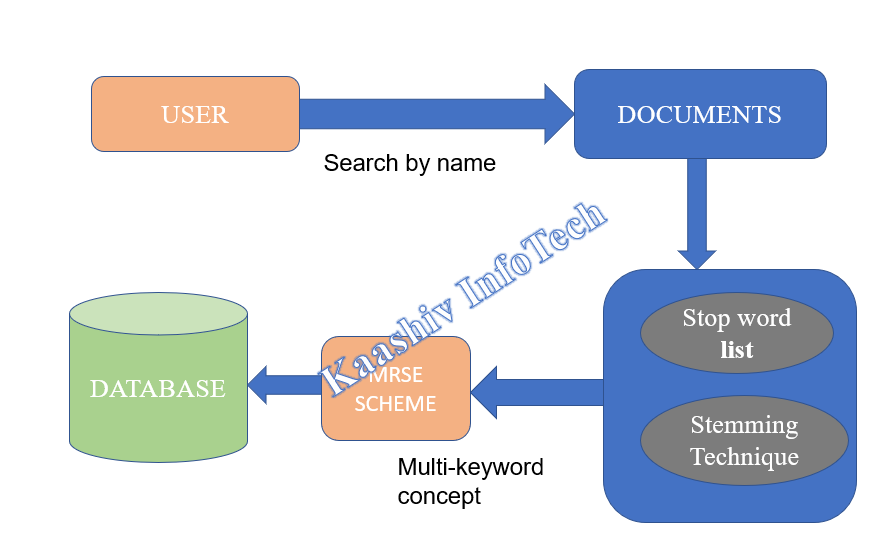
• Users search the document by using multiple keywords in a database.
• Removal of words in a database finally sorts out some multi-keywords for the document.
• These Multi-keywords are sorted by means of using priority basis.
• Multi-keyword ranked search over encrypted(MRSE) data is a technique involved and returning files in a ranked keyword order regarding to certain relevance criteria(eg:keyword frequency)
• Once the user checks about documents they are getting contents of various pages as a output .
• User wants to do the updation in particular page in a document, each page searched in a database and particular page is sorted out first and it is modified by the user.
• Those modification of particular page is done by using check sum technique in a database.
• It checks the pages and giving priority to the content.
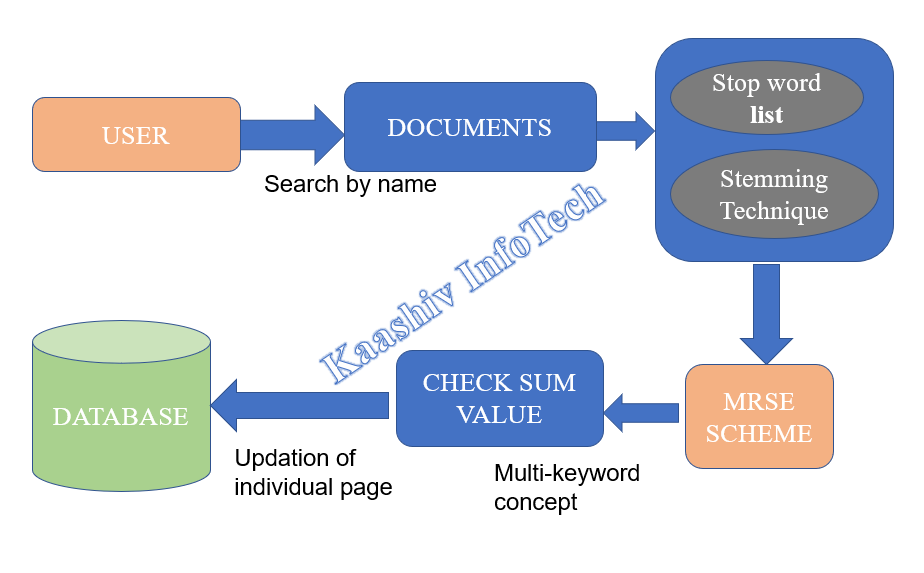
• User searched the document by using multi-keywords and finally outputs produced based on large number contents.
• Each and every content in a page is analyzed in a document and priority given to huge pages in a database.
• Priority wise pages are sorted in this module and cost is reduced because of using this technique in a cloud server.
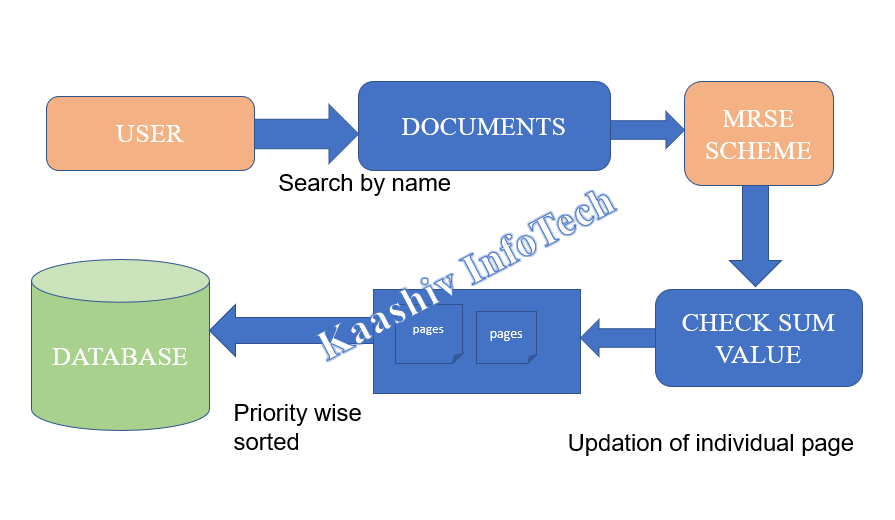
4. USER DOCUMENT REQUESTING MODULE:
-
• Users will be permitted to search for the document and in case if the user needs a document to be viewed. A request needs to be sent to the document owner.
• An automated email will be sent to the document owner to request access for the document.
• In this module, we are trying to use gmail SMTP to send emails.
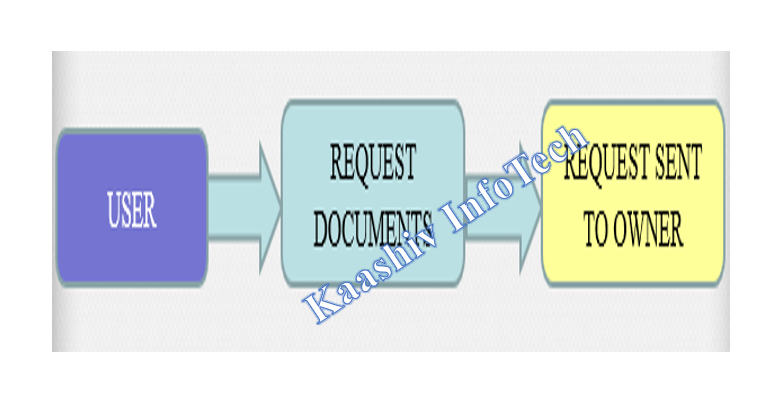
5. OWNER DOCUMENT APPROVAL MODULE:
-
• Once the document is requested by an user, the request will be received the document owner.
• Owner got the rights of approving or disapproving the document request.
• In case, if the owner approve the request, there is a checksum password reach the end user who requests the document.
• This checksum value is created with MD5 encryption algorithm.
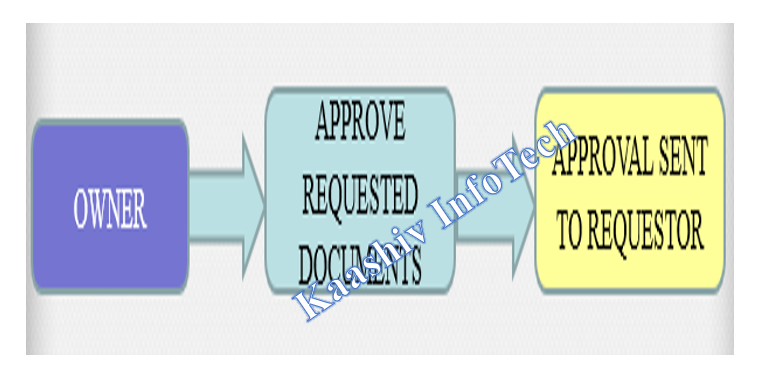
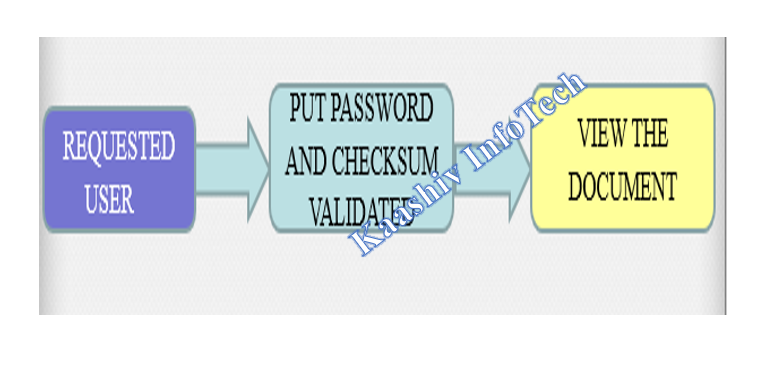
6. DOCUMENT VIEW MODULE:
• If the requested document is approved by the owner, the requested user can access the document through the password.
• Once the approval is done, an automated email with the checksum value password sent to the requested user.
• The password needs to placed by the end user to access the document. Now, he is able to view the document requested.
• In case rejected requests don’t have any access to the documents.
ISO CERTIFIED - FINAL YEAR PROJECTS :
KaaShiv Offers, Final year project . Final year project includes BlockChain, Python, IOT, Machine Learning, Data Science, Big Data, EthicalHacking, CCNA . This internship includes the topics related to final year projects for 2nd year students , final year projects for 3rd year students , final year projects for year students , final year projects for 4th year students.This company runs by,
• 10 Years Awarded Microsoft Most Valuable Professional
• Google Recognized Experts
• Cisco Recognized Certified Experts
• Microsoft Awarded Certified Experts
• Robotics Experts
• HCL Technologies Awarded Expert
Trainers at KaaShiv InfoTech are real-time Software / IT professionals worked in leading MNCs like,
• CTS
• Wipro,
• TCS,
• Infosys,
• Accenture and
• Mindtree.
The Course curriculum for Final year project is carefully researched and prepared by professionals from MNC to meet the demands expected in the IT industry. After completing the Final year project Training in Chennai at KaaShiv Infotech, students will be familiar with the Software development process followed in IT industry. Below are some of the insights of our Final year project program ,
• Real-time project development and Technology Training by Microsoft Awarded Most Valuable Professiona
• Final year project students involves Full practical training
• Hardware and software tools full support
• Technology training
• Placement training
• Full documentation and report analysis
• R & D projects
• Industrial exposure
• Endorsing Corporate skills
WHAT IS FINAL YEAR PROJECT ?
• The Final year projects plays a crucial role in the teaching-learning process.
• It is also a way of identifying the ability of the student to perform an industrial project or applied research linked to the knowledge discipline.
• A project is defined as an effort to create or modify a specific product or service.
• Projects are temporary work efforts with a clear beginning and end.
• Final year project (or program) any undertaking, carried out individually or collaboratively and possibly involving research or design, that is carefully planned (usually by a project team) to achieve a particular aim
WHAT ARE THE BENEFITS GAINED BY DOING FINAL YEAR PROJECT
• final year projects if done well can add a lot of credibility to your profile.
• And especially your final year projects building experience can help you perform well in core job placements & higher studies admission interviews.
TIPS TO SELECT GOOD FINAL YEAR PROJECTS
>
• Analyze the current trends
• Focus your final year project on any social issue
• Get expert’s assistance whenever possible
• Research about the final year projects done by your seniors
• Refer the research journals published by scholars
• Check the feasibility of your final year project
• Work with organizations like Kaashiv InfoTech
WHY, STUDENTS FINAL YEAR PROJECTS SHOULD BE A REAL TIME FINAL YEAR PROJECTS ?
Final year project students provides a real time exposure for the Final year project students on the latest and trending technologies. Below are some of the Top jobs in the IT Industry Job Openings ,
• Software Developers – Good in Python, Machine Learning, Data Science and AI programming
• BlockChain Administrators
• IOT Specialists
• Cyber Security
• Web Application Developer – Web Designers
• Information Security Analyst – Security Specialist
• Network Engineers / Analys
KaaShiv Infotech, Final year project Student - programme hornes you in the above said skills / job roles from basics to Advanced.
FINAL YEAR PROJECT - PROGRAMME HIGHLIGHTS
• Final year project program duration: 5days/ 10days / Or Any number of days
• Training hours: 3hrs per day
• Software & others tools installation Guidance
• Hardware support
• Final year project Report creation / Project Report creation
• Final year project students based 2 projects ( real time)
• Final year project Certificate & Inplant Training Certificate & Industrial exposure certificate + (Achievement certificate for best performers)
ADVANTAGES OF OUR- FINAL YEAR PROJECT
• Get Real Work Experience
• Get a Taste of Your Chosen Field
• Start Networking
• Helps You Choose a Speciality
• Helps You Become More Self-Confident
• Boosts Your CV
• Increases Your Market Value
FINAL YEAR PROJECT - MATERIALS
• Final year project student , includes Materials after the internship programme
• Technological guidance and materials will be shared in entire year for the students to mold technically.
• Our be student involves Free Projects at the end of the programme.
QUERIES OR CONTACT DETAILS :
Venkat (7667662428) and Asha (7667668009)
EmailID:kaashiv.info@gmail.com ,
priyanka.kaashiv@gmail.com
FINAL YEAR PROJECT - PROGRAMME DURATION :
1 months / 2 months / 3 months to 6 Months ( Any Number of Days - Based on student preferences)
WHO CAN ATTEND THIS FINAL YEAR PROJECT PROGRAMME :
final year project - Programme can be attended by the students who are looking for final year project / final year project 2nd year/ final year project 3rd year/final year project 4th year.
FINAL YEAR PROJECT - PROGRAMME OUTCOME :
1. Student will be specialized in Block Chain, Artificial Intelligence, Machine Learning, Python and R programming, Application Development
, Web designing and Networking concepts (Basics to Advanced)
2. Covering 45 concepts
3. Students will be getting trained in / writing 45 Programs – Will change based on the durations of the program.
4. 2 Projects and project documents will be given at the end of the program
REFERENCE YOUTUBE URL FOR FINAL YEAR PROJECT :
Check our Internship Training sample videos at this URL –
Check our Internship Training sample videos
REGISTRATION LINK FOR – FINAL YEAR PROJECT :
final year project - Offline - Office training
Fill our online Internship form
FINAL YEAR PROJECT – DEMO LINK :
Check out our Sample final year project Content for the training
inplant-training-in-chennai-for-cse-demo
CHECK OUR PREVIOUS TESTIMONIALS FROM STUDENTS FROM DIFFERENT COUNTRIES AND DIFFERENT STATES :
www.kaashivinfotech.com/testimonials/
CHECK OUR STUDENTS FEEDBACK ON OUR - FINAL YEAR PROJECT :
final year project - Feedback - inplant-training-feedback /
final year project - Feedback - internship-feedback
CHECK OUT THE COLLEGES ATTENDED OUR FINAL YEAR PROJECT
internship-and-inplant-training-attendees/
CHECK OUR SOCIAL SERVICE YOUTUBE CHANNELS :
Check our Social Service youtube channels
Check our Social Service youtube channels
REAL TIME PROJECT :
We ranked Top 200 technological companies in Tamil Nadu, Click here to view
MORE ON OUR, FINAL YEAR PROJECT :
In our, internship on final year - programme below are following different kind of programmes focused such as,
1. Final year project (or) paid Final year project,
- Kaashiv Provides an in-depth knowledge of software Platform and other relevant software technologies.
2. Final year project work from home – Our company provides facility for the students to learn from home as an Final year project based on latest technological trends.
3. Final year project report – Reports are also provided for the final year projects for students in our company related
4. Final year project jobs – 100% Job assistance will be provided for the students to gain practical knowledge during the Final year project period in our company.
5. Final year summer / Winter internship 2019/2020 – Summer / Winter holiday internship in Final year projects will be given to the student based on the developer knowledge base.
6. Final year project interview questions – We provide top trending and frequently asked question for the intern students during the internship period based on software development and trending technologies.
7. Final year project test – Based on the students request, if you are looking for any test to validate your knowledge. we are ready to provide the same.
8. Final year project certificate – Industry recognized certificates will be provided for the students who perform internship in our company based .
9. Final year project online– Learn Final year projects from home, our company perform internship through online too.
10. Final year project ppt / final year projects / projects report – We provide Final year projects based ppts. projects and project reports as materials after the internship in our company.
11. Free final year project - Our company will provide free Final year projects for the best students of kaashiv infotech.
12. Project For Diploma Final year projects – We offer project for the diploma Final year project students in our company.
13. Final year project For 2nd Year / 3rd Year / B-Tech Students – Our company offers you final year project for the above students.